Office 365 Enterprise Mobility and Security
Cybersecurity has never been more on the forefront of global technological advancement as it has been now, especially for mobile security. Cyber threats have morphed into aggressive and complex attacks, and Microsoft’s mission is to empower every person and every organization to shut down cyber threats before they become attacks by providing first defenders the tools to do so with Microsoft 365’s core component Office 365 Enterprise Mobility + Security.
Office 365 Enterprise Mobility + Security (EMS) leverages artificial intelligence to provide intelligent mobility management and a security platform by increasing the security features in Office 365 and extends them across the entire environment, including third-party investments. Not only does EMS empower your employees with mobile flexibility but it secures your organization and protects its data.
The face of cyber threats and attacks change daily, resulting in challenges that are faced in securing the data environment. The first is the creativity and complexity of attacks that are now being formulated. These are more complex than the simple, identify theft that we are familiar with, though this is the step of how they gain access to your data. Digital access is global, and users can tap into information wherever they are, including stationary at a desk to moving in a car. The vastness of the digital real estate, by itself, is difficult to secure. Though we are advancing with faster, more trustworthy, and more intelligent technology, it is still expensive and time-consuming to manually correlate actions on threat and attack signals.
Office 365 EMS consists of five groups with actions to provide enterprise mobile security. These five core groups are:
- Identity and Access Management;
- Information Protection;
- Threat Protection;
- Unified Endpoint Management; and
- Cloud Access Security Broker.
Identity and Access Management
Identity theft is one of the many methods to breach data security. With EMS, there are several ways to help reduce the possibilities of data breaches with tighter requirements for identity to gain access. Access management can be enforced through several venues, including:
Securing Authentication: The one-word password for authentication no longer provides secure and guaranteed access as it once did. With the advancement of technology, the methodologies for cyber threats have also advanced. Combining software, artificial intelligence, and science, there are new ways of managing access to secured data. These include:
- Going Without a Password utilizes biometrics for authentication;
- Multi-Factor Authentication keeps user identities safe, the current rate at the time of publication is 99.9%;
- Password Protection in Azure AD bans password lists and provides smart lockout features to help safeguard credentials; and
- Windows 10 – Secure Identity and Access provides control access to mitigate credential theft in Windows 10.
Govern and Protect Access: Microsoft’s “Never trust, always verify” is an apt motto when it comes to protecting and governing access. With Azure AD conditional access, Zero Trust can be delivered:
- Enable Secure Productivity by controlling data access based on the location of the user, the device, applications that are offline, and proactively determining the risk of the environment. Access modes can be secured in SharePoint Online, Microsoft Cloud App Security, and Exchange Online;
- Secure and Manage Endpoints through Azure AD conditional access, Microsoft Intune and Windows Defender ATP. Working together, Azure AD and Microsoft Intune ensure that only managed and compliant devices are allowed access to Office 365 services, email, SaaS apps, and on-prem apps;
- Secure Administration with Azure AD with Privileged Identity Management which secures admin accounts across Office 365 and Azure; and
- Azure AD Identity Governance ensures the identity, access, and admin lifecycle governance.
Obtain Comprehensive Identity Protection: Prevent identity attacks by implementing Microsoft Cloud Security, Azure AD Identity Protection and Azure ATP by:
- Securing Identity Infrastructure by following these five steps: strengthen your credentials, reduce your attack surface, automate threat response, increase your awareness, and enable end-user self-help;
- Identity Security Insights obtained with Azure AD Identity Protection detects risks and provides you the opportunity to define policies for remediation. Once an upcoming attack is spotted, the doors of access can be locked by using the What-If Tool, implementing Conditional Access, customizing and accessing the Security Dashboard, defining Identity Protection and generating security reports;
- Hybrid Identity Forensics combines the security measures in Azure ATP and Microsoft Cloud App Security, guarding against threats on-prem and in the cloud; and
- Long term security is a peace of mind with Identity in Microsoft Secure Score which provides the latest guidance on new threats that evolve on daily.
Information Protection
Protect Your Data: Whether being shared or being toted on the go, protect your sensitive data everywhere by controlling how a file is being used by:
- Identifying, Understanding and Discovering sensitive data across all apps, devices, and services including cloud and on-prem;
- Customizing Information Protection Policies by classifying and labeling documents based on sensitivity labels that you define. Configure protection actions such as access restrictions, visual markings, and encryption;
- Analyzing How Users Access and Share Sensitive Data in cloud services. By gaining insight, access to protected files can be revoked while policy violations and risky behaviour can be monitored; and
- Accelerating the Path to Compliance by enhancing privacy and security in compliance with the General Data Protection Regulation (GDPR) and other regulatory requirements.
Threat Protection
Integrate and Automate Security by:
- Protecting Against Threats by detecting and investigating compromised identities, advanced threats, and malicious actions across cloud environments and on-prem; and
- Securing identities so that malicious logins are blocked and threats are locked down, securing email, apps, documents, and data with the help of analytics to prevent phishing and 0-day attacks, securing endpoints with automated investigations to alerts and execution of remedial actions to threats, and securing the hybrid cloud infrastructure by safeguarding information, data, and servers from attacks by quickly detecting and blocking malicious activity running in the cloud or on-prem with advanced analytics.
Unified Endpoint Management with Microsoft Intune
- Support diverse mobile ecosystems by streamlining and automating deployment, provisioning, app delivery, updates, and policy management to iOs, macOS, Android, and Windows devices;
- Attain IT efficiency in the cloud through leveraging insights and baselines for security policies and configuration settings in a scalable globally distributed cloud service architecture; and
- Protect data with or without device enrolment continues on mobile devices through granular control over Office 365.
Microsoft Cloud App Security – Cloud Access Security Broker (CASB)
- Multimode Microsoft Cloud App Security integrates with leading Microsoft solutions to provide simple deployment, innovative automation, and centralized management; and
- CASB consists of the following:
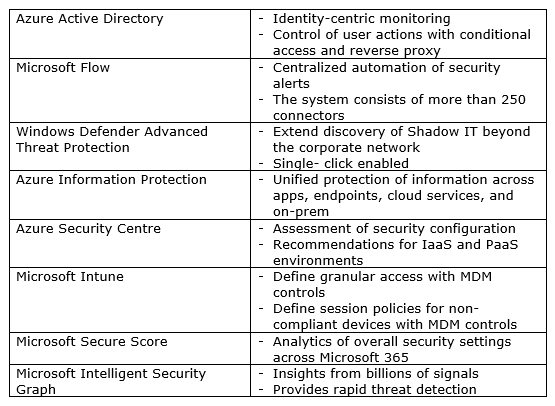
Specialized Products in Office 365 EMS
- Azure Active Directory – protects user credentials while allowing users to connect to apps in a secure method;
- Microsoft Intune – cloud-based unified data protection, access management, and endpoint management;
- Azure Information Protection – cloud-based data classification, protection, encryption, and tracking;
- Microsoft Cloud App Security – a multi-node CASB providing behavioural analytics, data protection, risk management, discover, and threat protection;
- Microsoft Advanced Threat Analytics – protection against advanced and targeted attacks and insider threats for on-prem; and
- Azure Advanced Threat Protection – cloud-based solution to identify, detect and investigate compromises, threats, and malicious actions.
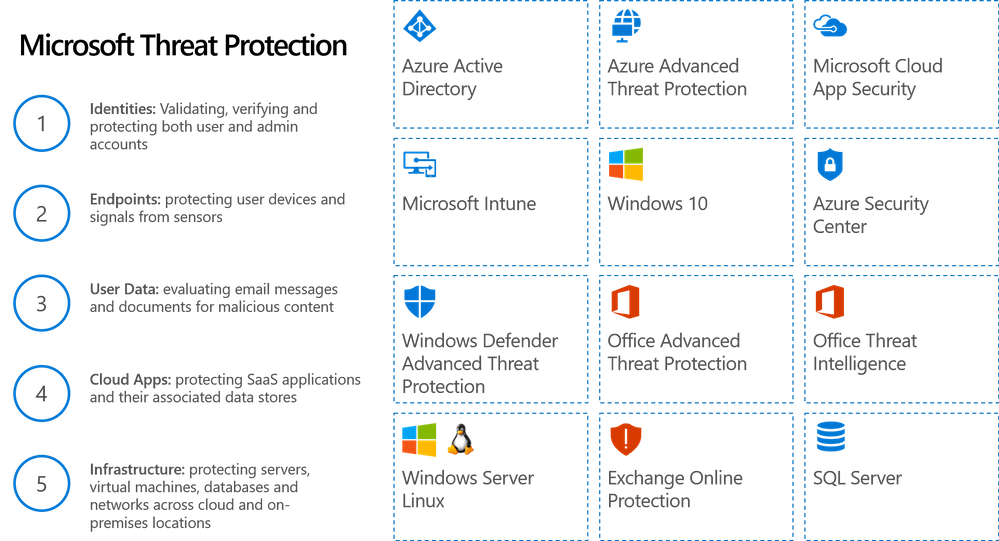
There is no one single software that can provide extensive and complete defences for increasingly complex forms of cyber threats and attacks. A tight defence requires a combination of several services that provide solutions to possible penetrations points, thereby working synergistically to provide full protection. Each group of solutions provides protection from different attack vectors, providing maximum coverage for security. With Office 365 Enterprise Mobility and Security, a comprehensive, end to end and fully integrated enterprise solution is provided for mobile security on devices, in the cloud, and on-prem.
 Saturday, February 09, 2019
By : Mike Maadarani
Saturday, February 09, 2019
By : Mike Maadarani
 0 comment
0 comment
Archives
- December 2024
- November 2023
- October 2023
- September 2023
- August 2023
- January 2023
- November 2022
- October 2022
- May 2022
- March 2022
- January 2022
- December 2021
- November 2021
- October 2021
- March 2021
- October 2020
- September 2020
- July 2020
- March 2020
- February 2020
- January 2020
- December 2019
- November 2019
- October 2019
- September 2019
- June 2019
- May 2019
- March 2019
- February 2019
- January 2019
- December 2018
- November 2018
- October 2018
- September 2018
- August 2018
- July 2018
- June 2018
- May 2018
- April 2018
- March 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- August 2017
- July 2017
- June 2017
- May 2017
- March 2017
- February 2017
- January 2017
- October 2016
- September 2016
- August 2016
- July 2016
- June 2016
- May 2016
- March 2016
- February 2016
- January 2016
- September 2015
- August 2015
- July 2015
- June 2015
- April 2015
- February 2015
- January 2015
- November 2014
- October 2014
- September 2014
- November 2013
- July 2013
- February 2013