Configuring Hybrid Infrastructure
Setting up SharePoint on-premises requires that you meet basic SSO deployment requirements and then configure SharePoint 2013 services and inbound requests.
When you set up and enable SSO, users in your organization are able to use their corporate credentials to access the Office 365 service offerings. This removes the burden of managing multiple logon identities and passwords. Without SSO, an Office 365 user would have to maintain separate user names and passwords. For an even better end-user experience, you can create and deploy smart links, which can help speed user sign-in requests by reducing the number of redirects necessary for authentication.
In addition to user advantages, administrators and the organization can also benefit from SSO. For example, configuring SSO helps to enforce the organization’s password policies and account restrictions in both the on-premises directory and the Office 365 directory.
To prepare, you must make sure the environment meets the requirements for SSO and verify that the Active Directory and Azure Active Directory tenant is set up in a way that is compatible with single sign-on requirements. Also, Active Directory must be deployed and running in Windows Server 2003 R2, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, or Windows Server 2012 R2 with a functional level of mixed or native mode. If you plan to use AD FS as your STS, you will need to do one of the following:
- Download, install, and deploy AD FS 2.0 on a Windows Server 2008 or Windows Server 2008 R2 server.
- Deploy an AD FS 2.0 proxy, if users will be connecting from outside the company network.
- Install the AD FS role service on a Windows Server 2012 or Windows Server 2012 R2 server.
In addition, Active Directory must have certain settings configured to work properly with single sign-on. In particular, the UPN, or the user logon name, must be set up in a specific way for each user.
Configure SharePoint 2013 services
You need to configure the User Profile Service to synchronize user and group profiles from the on-premises Active Directory domain. When federated users access resources in a hybrid environment, the STS makes calls to the User Profile Service to obtain user account metadata, such as the UPN and email property values. This metadata is used by the STS to construct security tokens during the authentication process.
SharePoint Online presents claims to the on-premises SharePoint farm by using the Simple Mail Transfer Protocol (SMTP). To support this, you need to ensure that the SharePoint user profiles for all federated users are populated with the user’s email address by using the correct UPN.
This means that the work email field in the on-premises SharePoint User Profile Store needs to contain the user’s federated email address. For example, if a federated user logs on to the on-premises domain as contoso\karenb and the public domain for the hybrid environment is contoso.com, her federated email address is karenb@contoso.com.
You must verify that the App Management and Microsoft SharePoint Foundation Subscription Settings services are started and configured. These services must be enabled to support certain configuration procedures, and to help register SharePoint Online as a high-trust application in SharePoint 2013.
Configure SharePoint 2013 for inbound requests
If the hybrid environment is configured for an inbound authentication topology, you must ensure that a single on-premises web application is configured to receive requests from SharePoint Online. This web application is referred to as the primary web application for the hybrid environment, and it accepts requests from the external endpoint URL. No specific web application configuration is required to support a one-way outbound authentication topology.
In a SharePoint Server 2013 hybrid environment, outbound connections can be made from any on-premises web application. A single SharePoint Server 2013 web application must be configured for inbound connections; it is used as the primary web application for accepting inbound connections and configuring services and connection objects for the hybrid features you deploy. You can either create a new web application and site collection or configure an existing web application for this purpose.
Configure SharePoint Online
Setting up SharePoint Online requires that you choose an application authentication topology and make additional configuration choices for the service.
Choose authentication topology
As shown in Figure 1, your choice of an authentication topology determines how certificates are configured and what capabilities are present in the hybrid solution.
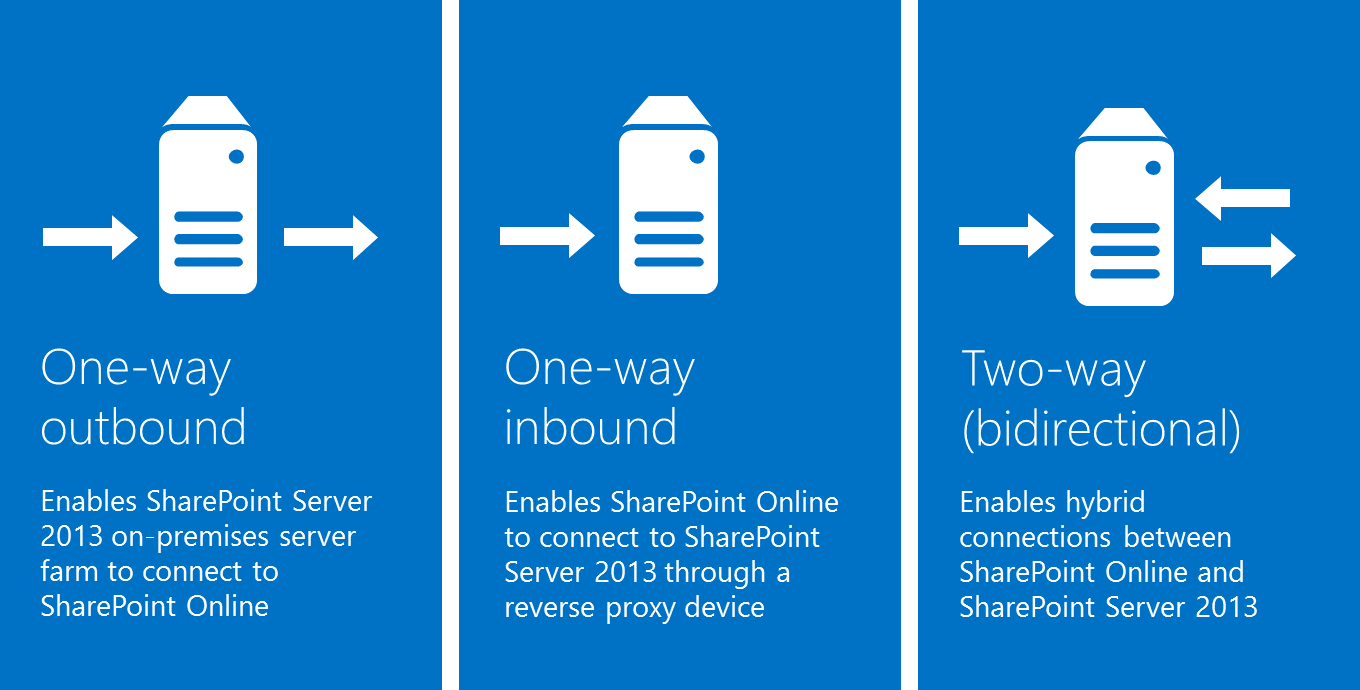
Figure 1: Application authentication topologies
One-way outbound topology
One-way outbound topology is not supported with hybrid BCS. Only one-way inbound and two-way (bidirectional) topologies.
One-way inbound topology
A one-way inbound hybrid topology enables SharePoint Online to connect to SharePoint Server 2013 through a reverse proxy device (Figure 2). For example, users of a SharePoint Online Search portal can see both local and remote search results, but only local results are available in the SharePoint Server 2013 Search portal.
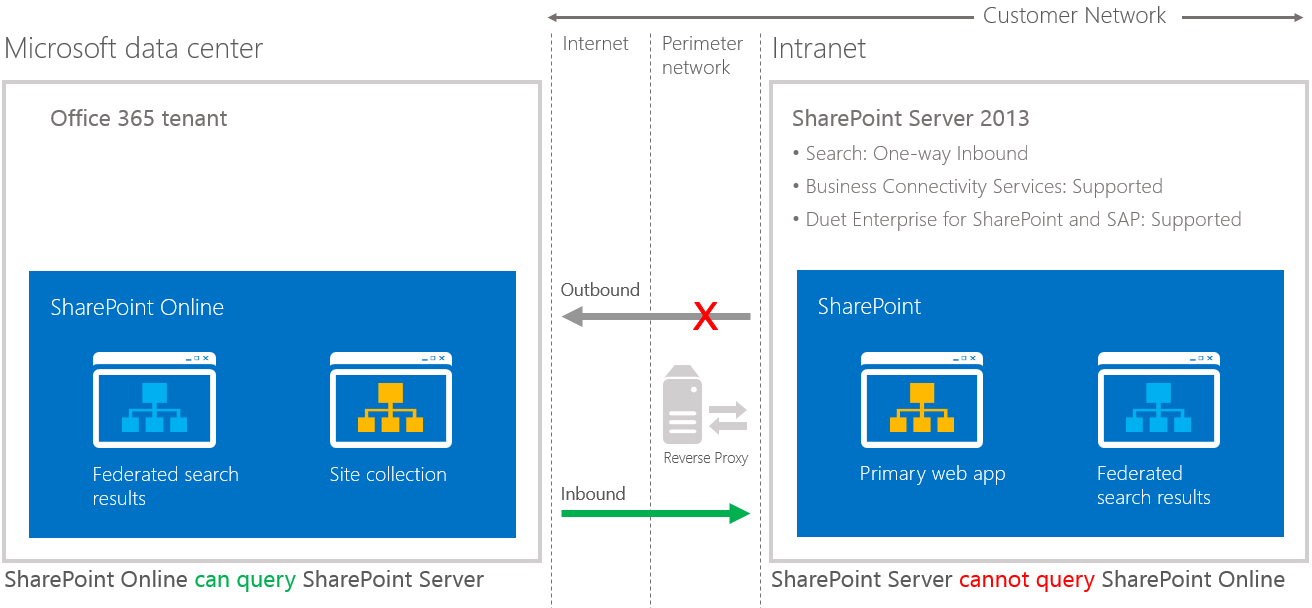
Figure 2: One-way inbound topology
A one-way inbound topology can be configured to let users access on-premises SharePoint search results from the Internet, as long as they have access to the intranet through a virtual private network or DirectAccess.
- On-premises SharePoint Server 2013 Enterprise Search portal: Local search results are available
- SharePoint Online Search portal: Local and remote search results are available
Two-way (bidirectional) topology
A two-way topology enables bidirectional hybrid service integration between the on-premises SharePoint Server 2013 farm environment and the Office 365 tenant (Figure 3). For example, search can be configured to allow federated users to see both local and remote search results in either SharePoint Server 2013 or SharePoint Online Search portals.
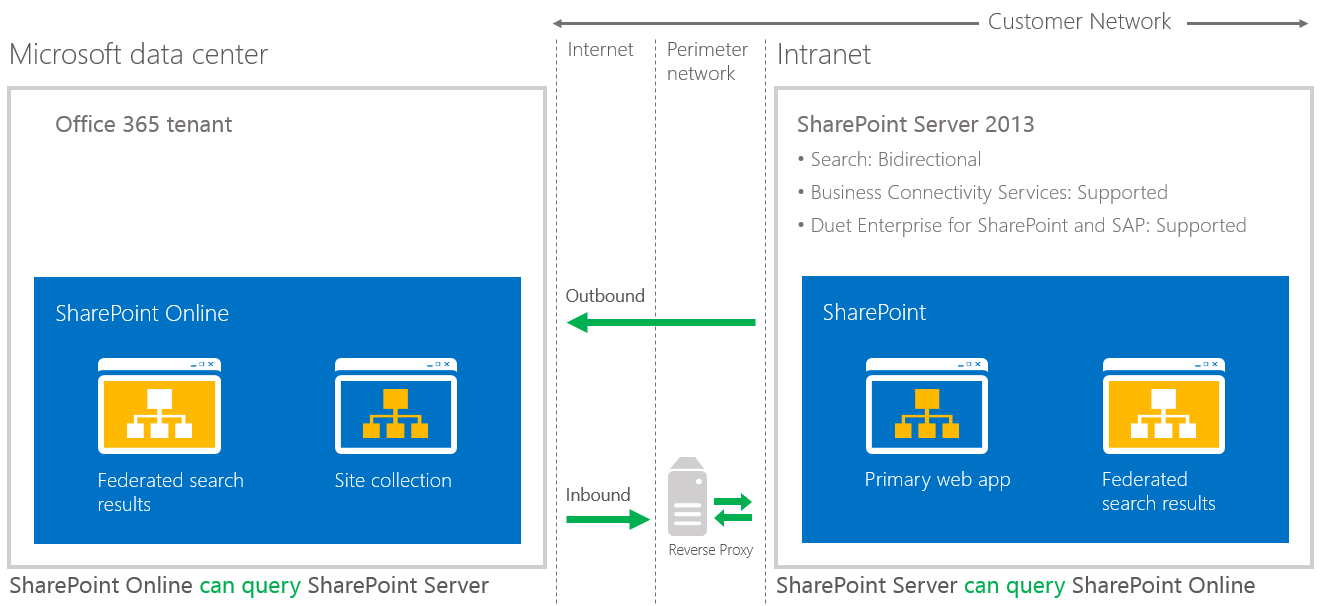
Figure 3: Two-way (bidirectional) topology
A two-way topology can be configured to let users access on-premises SharePoint search results from the Internet, as long as they have access to the intranet through a virtual private network or DirectAccess.
- On-premises SharePoint Server 2013 Enterprise Search portal and SharePoint Online Search portal: Local and remote search results are available.
- If extranet authentication services are configured, extranet users can log on remotely through an on-premises Active Directory account and use all available hybrid functionality.
Refer to these articles to configure your reverse proxy server and how to establish a secure connection between your Online and on-premises tenants.
| Link to procedure | Description of procedure |
| Configure a one-way inbound hybrid topology | Learn how to configure the infrastructure for SharePoint 2013 hybrid environments that use a one-way inbound authentication topology. |
| Configure a two-way bidirectional hybrid topology | Learn how to configure the infrastructure for SharePoint 2013 hybrid environments using a two-way authentication topology. |
 Monday, August 24, 2015
By : Mike Maadarani
Monday, August 24, 2015
By : Mike Maadarani
 0 comment
0 comment
Archives
- December 2024
- November 2023
- October 2023
- September 2023
- August 2023
- January 2023
- November 2022
- October 2022
- May 2022
- March 2022
- January 2022
- December 2021
- November 2021
- October 2021
- March 2021
- October 2020
- September 2020
- July 2020
- March 2020
- February 2020
- January 2020
- December 2019
- November 2019
- October 2019
- September 2019
- June 2019
- May 2019
- March 2019
- February 2019
- January 2019
- December 2018
- November 2018
- October 2018
- September 2018
- August 2018
- July 2018
- June 2018
- May 2018
- April 2018
- March 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- August 2017
- July 2017
- June 2017
- May 2017
- March 2017
- February 2017
- January 2017
- October 2016
- September 2016
- August 2016
- July 2016
- June 2016
- May 2016
- March 2016
- February 2016
- January 2016
- September 2015
- August 2015
- July 2015
- June 2015
- April 2015
- February 2015
- January 2015
- November 2014
- October 2014
- September 2014
- November 2013
- July 2013
- February 2013